Hi )))))))))))))
So here’s the deal: Microsoft just migrated its entire Windows Key Management Service (MKMS) — the backbone of license activations for Windows, Xbox, Office and who knows what else — into Azure.
Not just any Azure. We’re talking Confidential Virtual Machines, managed HSMs, and enough hardware-backed encryption to make even the NSA feel excluded.
🎯 What is MKMS and Why Should You Care?
MKMS is the silent monster that handles billions of license activations per day. Whenever you install Windows or something calls home to verify it’s legit — that’s MKMS doing its thing.
It used to live in Microsoft’s own private datacenters, surrounded by a mess of legacy hardware, HSM modules, and custom cryptography.
Now? They’ve tossed that mess into Azure Confidential Computing and slammed the door shut.
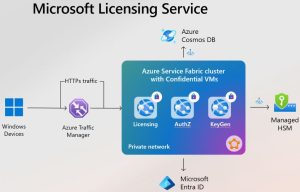
🔒 How Did They Lock This Down? (And It’s Not Just Marketing)
1. Confidential VMs with AMD SEV-SNP
These aren’t your average VMs. This is next-gen hardware-enforced encryption at the memory level. Everything inside the VM is sealed off — not even Azure admins can peek in.
This is possible thanks to AMD SEV-SNP: a silicon-powered Trusted Execution Environment (TEE) that encrypts and isolates everything — down to the CPU registers.
Zero Trust? Nah, this is Paranoid Trust. And that’s the point.
2. Managed HSMs — FIPS 140-2 Level 3
Microsoft’s now storing its keys in Azure-managed hardware security modules, certified to a level that screams “government-grade”.
These aren’t simulated crypto vaults — these are actual, isolated, tamper-proof physical devices. If you lose a key here, even Microsoft can’t recover it. Harsh? Yes. Secure? Absolutely.
3. Full-stack auditing from kernel to API
Every request, every VM start, every keystroke (figuratively) is logged, analyzed, traced and encrypted.
The telemetry is insane — security events now bubble up from the virtual firmware level all the way to Azure’s APIs.
It’s not just observability, it’s telepathic defense.
🧠 Why Did Microsoft Do This?
Easy:
-
💰 Cutting costs. Legacy datacenters are expensive and messy. Azure is cheaper, scalable, and easier to secure at cloud speed.
-
🧪 Proving Azure Confidential Computing is real. If Microsoft trusts it to guard its licensing revenue, so should you.
-
🌍 Global reach with low latency. No more bottlenecks in far regions — MKMS now rides on Azure’s global backbone.
Basically, Microsoft just ate its own security dog food — and told the world it’s delicious.
🧩 Can You Do This Too? (Technically Yes. Realistically… Read This First.)
Azure gives you access to the exact same tech: Confidential VMs, managed HSMs, enclave-backed workloads. But:
-
🧠 You need serious architecture chops. This isn’t a “deploy and forget” scenario — this is SecureOps on nightmare mode.
-
💸 It’s not cheap. CVMs run on specialized hardware (DC-series, H-series), and managed HSMs are billed like they’re made of gold.
-
😬 Mistakes are brutal. Delete a key? It’s gone. Misconfigure access? You’re locked out. Microsoft won’t save you.
💥 TL;DR (Without the TikTok Voiceover)
Microsoft migrated its Windows licensing backend (MKMS) into Azure Confidential Computing, combining:
-
🔐 Confidential VMs (AMD SEV-SNP)
-
🔐 Managed HSM (FIPS 140-2 Level 3)
-
📊 End-to-end auditing and telemetry
And they didn’t just try this — they went all-in on the thing that literally prints money for them. If that’s not a vote of confidence in their own tech, what is?
Final Thoughts
This isn’t just a cool use case.
This is Microsoft dogfooding cloud security on the most mission-critical system it owns.
Licensing is money. And now, that money lives in Azure, inside a locked-down, hardware-isolated vault.
So the next time someone asks if Confidential Computing is production-ready, just drop this on the table.
