hi. u ever looked at a flat vnet setup with 20 peered networks and thought: this looks like my first mind map in 6th grade? yeah, same.
it’s a mess. routing breaks, security groups overlap, traffic gets lost in space. and try explaining it to a new hire? forget it.
so let’s fix it. enter: Hub-spoke topology. Azure-native. battle-tested. enterprise-friendly. and—get this—actually makes sense.
what is hub-spoke, really?)
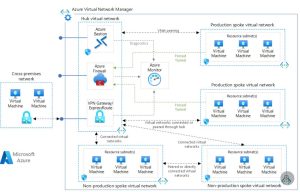
ok, imagine ur network like a wheel.
– the hub is the center — a shared core vnet with stuff like firewalls, VPNs, bastion, logging.
– the spokes are vnets for each business unit, app, or region. they connect to the hub, but not directly to each other (unless u say so).
hub controls everything.
spokes stay clean, isolated, and organized.
more here if u want diagrams and official-sounding words:
https://learn.microsoft.com/en-us/azure/architecture/networking/architecture/hub-spoke
why bother?
’cause flat peer-to-peer vnet meshes are nightmares.
every vnet needs to peer with every other. u hit transitive routing issues. ur NSGs become spaghetti. troubleshooting becomes CSI: Cloud Edition.
hub-spoke fixes that:
– centralized routing
– clean segmentation
– shared security services
– easy-to-scale architecture
– no overlapping IP hell
plus, it’s what actual grown-up networks look like. the ones that survive audits and compliance reviews without people sweating.
ok but what lives in the hub?)
usually stuff like:
– Azure Firewall or third-party NVA (next-gen firewall)
– VPN gateway / ExpressRoute gateway
– Azure Bastion
– Azure Monitor agents / SIEM forwarders
– Private DNS zones
– Application Gateway or Azure Front Door
– Jumpboxes, NAT, maybe identity proxies
basically: anything that should be shared across environments, secure by design, and tightly controlled.
the hub doesn’t run apps. it runs infrastructure.
it’s ur fortress core.
and the spokes?)
spokes are where the action happens. app workloads. dev/test envs. isolated teams. staging. prod.
each spoke is a separate vnet. u can give it its own NSGs, route tables, UDRs, logging.
if u wanna keep HR away from finance? hub-spoke makes that easy.
also: u decide if spokes can talk to each other — via the hub, or not at all. default? no lateral traffic.
wanna open it? route it explicitly. that’s control. that’s good design.
how do they talk to each other?)
u set up vnet peering between the hub and each spoke.
Azure does the heavy lifting with the System Routes, and u can override with UDRs (User Defined Routes) when needed.
bonus points:
– enable gateway transit on the hub → spoke can use VPN/ER
– use route tables to force spoke→hub→internet (forced tunneling)
– inspect egress via Azure Firewall or NVA
– collect logs centrally via Log Analytics workspace in hub
and yes, this might help in other clouds too — AWS has similar with TGWs, and GCP’s VPC peering sorta works the same way. just… Azure’s is cleaner out of the box.
security loves hub-spoke)
NSGs on each spoke? check.
central firewall in hub? check.
Private Link traffic only? oh yes.
monitoring in one place? 100% yes.
Azure Policy + Defender for Cloud to enforce tagging, route auditing, port lockdown? get in.
the hub-spoke model makes it way easier to layer security — perimeter, subnet, host.
plus it simplifies Zero Trust design. each spoke is a microsegment.
wanna bring in identity-based access control or conditional routes? do it in hub. filter from there.
and scaling? smooth.
need new region? new spoke.
need new workload? new spoke.
need DR setup? mirror the spokes, reuse the hub infra.
each spoke can scale independently — its own IP range, NSGs, UDRs. u don’t touch the hub infra every time something new shows up.
also: AVS, AVD, App Services, AKS — all of these play well with this pattern. just wire them as spokes. that’s the beauty of it. modular by design.
can I automate this? pls say yes)
yes. yes yes. use:
– Bicep
– Terraform
– Azure CLI
– ARM templates (if u hate urself)
infra-as-code hub-spoke is a vibe. drop a new spoke with a script. peer it. deploy an app. done.
Azure Landing Zones even give u a ready-to-go module for this topology. check this out if u’re building from scratch or doing large-scale infra:
https://learn.microsoft.com/en-us/azure/cloud-adoption-framework/ready/landing-zone/
cost? minimal. benefit? huge.
the peering is cheap. the complexity reduction is priceless.
u save hours of troubleshooting, auditing, firewall hopping, support calls, and network spaghetti nightmares.
plus, with Azure Route Server, NVA integration, Private Link, and DNS forwarding, u get an enterprise-class design that still runs smooth on small- or mid-sized teams.
and this design helps u sleep better. cause when traffic breaks — u know where to look.
do I need to be on Azure to do this?
nah. the pattern itself is universal.
what changes is implementation.
u can build hub-spoke on AWS, GCP, even on-prem if u’re brave.
but on Azure? it’s native. fast to deploy. cheap to run. easy to monitor. secure by default.
plus it works great with Azure services like:
– Azure Firewall
– Microsoft Entra ID
– Azure Policy
– Microsoft Defender for Cloud
– Azure Monitor / Sentinel
– App Gateway / AFD
– Log Analytics
so yeah… worth doing right here.
ready to ditch flat vnets and build like a boss?)
go read this: https://learn.microsoft.com/en-us/azure/architecture/networking/architecture/hub-spoke
draw a diagram. build a PoC. start small — one hub, two spokes.
wire in monitoring. drop in a firewall. test it. scale it. and enjoy the sweet, sweet silence of infra that makes sense.
no more spaghetti. no more overlapping ranges. no more random subnet chaos.
hub-spoke is how u go from it works on my box to it scales for the org.
build it once. extend forever.
