Attackers are constantly looking for new vulnerabilities to exploit in Kubernetes environments. Recently, Microsoft uncovered an attack that takes advantage of new critical vulnerabilities in OpenMetadata to access Kubernetes workloads and use them for cryptocurrency mining.
OpenMetadata is an open-source platform that helps manage metadata across different data sources. It acts as a central repository for metadata, allowing users to find, understand, and control their data. In March 2024, some vulnerabilities in the OpenMetadata platform were disclosed. These vulnerabilities (CVE-2024-28255, CVE-2024-28847, CVE-2024-28253, CVE-2024-28848, and CVE-2024-28254) affect versions prior to 1.3.1 and can be exploited by attackers to bypass authentication and execute code remotely. Since April, we’ve seen these vulnerabilities exploited in Kubernetes environments.Microsoft strongly recommends that customers check clusters that are running OpenMetadata workloads and ensure that the image is updated to version 1.3.1 or later. In this blog post, we will share our analysis of the attack, provide guidance on identifying vulnerable clusters, and discuss how Microsoft security solutions such as Microsoft Defender for Cloud can be used to detect malicious activity. We will also share indicators of compromise that defenders can use for hunting and investigating.
Attack Flow
For initial access, attackers likely identify and target OpenMetadata workloads exposed to the internet. They then exploit a vulnerable version of the application to gain code execution on a container running the OpenMetadata image.
After establishing a foothold, attackers attempt to validate their intrusion and assess their control over the system. This step often involves contacting publicly available services. In this attack, attackers send ping requests to domains ending in oast.me and oast.pro, associated with Interactsh, an open-source tool for detecting out-of-band interactions.OAST domains are publicly resolvable but unique, allowing attackers to determine network connectivity from the compromised system to their infrastructure without generating suspicious outbound traffic that could trigger security alerts. This technique is useful for attackers to confirm successful exploitation and validate their connection with the victim before establishing a command-and-control (C2) channel and deploying malicious payloads.
After initial access, attackers run a series of reconnaissance commands to gather information about the victim’s environment. They query information about the network, hardware configuration, operating system version, active users, and more.As part of the reconnaissance phase, the attackers collected information about the environment in which the target workload is running. In the case of OpenMetadata, this information might include connection strings and credentials for services used by OpenMetadata, which could allow the attackers to access additional resources.
Once the attackers have confirmed their access and verified connectivity, they download a payload of cryptomining malware from a remote server. This server is located in China and hosts additional malware related to cryptomining that can be used on both Linux and Windows operating systems.
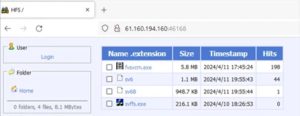
The downloaded file’s permissions are then changed to grant execution privileges. The attacker also left a personal message for the victim:
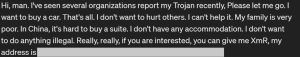
Next, the attackers execute the downloaded malware related to crypto mining, and then delete the initial payloads from the system. Finally, for keyboard activity, the attackers establish a reverse shell connection with their remote server using the Netcat tool, allowing them to access the container remotely and gain more control over the system. Additionally, to ensure persistence, the attackers use cronjobs for task scheduling, which enables the execution of malicious code at predefined intervals.
To check if your cluster is vulnerable, administrators who run Open Metadata workloads in their clusters need to ensure that the image is updated. If Open Metadata is exposed to the internet, it is recommended to use strong authentication and avoid using default credentials. To get a list of all images running in the cluster, administrators can use the following command:
kubectl get pods –all-namespaces -o=jsonpath='{range .items[*]}{.spec.containers[*].image}{“\n”}{end}’ | grep ‘openmetadata’
If there is a container with a vulnerable image, it is important to update the image to the latest version to ensure security. Microsoft Defender for Cloud can help with this process.
This attack reminds us of the importance of staying compliant and running fully patched workloads in containerized environments. It also emphasizes the significance of a comprehensive security solution like Microsoft Defender for Containers, which can detect malicious activity when a new vulnerability is exploited in an attack. In this instance, Microsoft Defender alerts were triggered by the attackers’ actions, identifying the malicious activity within the container. An example of this is when Microsoft Defender alerted about an attempt to start a reverse shell from a container within a Kubernetes cluster, similar to what happened in this incident.
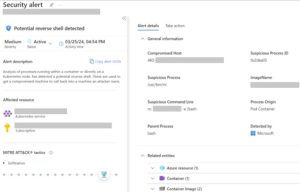
To prevent such attacks, Microsoft Defender for Containers provides an agentless vulnerability assessment for Azure, AWS, and GCP. This allows you to identify vulnerable images in your environment before an attack occurs. Microsoft Defender Cloud Security Posture Management (SPM) can help prioritize security issues based on their risk. For example, MS Defender CSPM can highlight vulnerable workloads that are exposed to the internet, so organizations can quickly remediate critical threats.
Additionally, organizations can monitor Kubernetes clusters using Microsoft Sentinel via the Azure Kubernetes Service (AKS) solution. This provides a detailed audit trail of user and system activities to identify malicious behavior.
Indicators of compromise (IoCs)
| Type | IoC |
| Executable SHA-256 | 7c6f0bae1e588821bd5d66cd98f52b7005e054279748c2c851647097fa2ae2df |
| Executable SHA-256 | 19a63bd5d18f955c0de550f072534aa7a6a6cc6b78a24fea4cc6ce23011ea01d |
| Executable SHA-256 | 31cd1651752eae014c7ceaaf107f0bf8323b682ff5b24c683a683fdac7525bad |
| IP | 8[.]222[.]144[.]60 |
| IP | 61[.]160[.]194[.]160 |
| IP | 8[.]130[.]115[.]208 |