Effective Date: June 15, 2025
New IP Subnet: 51.5.0.0/16
Microsoft is expanding the global infrastructure supporting RDP Shortpath by introducing a dedicated TURN relay IP range across 40 Azure regions. This update is a major leap in performance and reliability for Windows 365 and Azure Virtual Desktop (AVD), particularly in environments with strict network policies or high-latency paths.
🔍 What Is TURN and Why It Matters?
TURN (Traversal Using Relays around NAT) is a protocol enabling UDP-based connectivity for clients behind firewalls and NAT devices. In Microsoft’s implementation of RDP Shortpath for public networks, TURN serves as a fallback mechanism when direct UDP connectivity cannot be established.
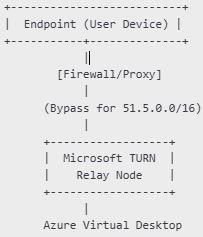
With this update, Microsoft is moving TURN relay traffic from the current ACS range (20.202.0.0/16) to a new, dedicated IP block (51.5.0.0/16) that is part of the WindowsVirtualDesktop service tag—simplifying firewall and routing configurations at scale.
🌐 Regional Expansion: From 14 to 40 Regions
The infrastructure scale-out means relay nodes are now closer to users geographically, improving performance and resiliency:
| Improvement | Impact |
|---|---|
| Lower Latency | Faster round-trip times and better session responsiveness |
| Higher Reliability | Reduced connection drops, particularly over variable networks |
| Improved UDP Success Rate | Better handling of real-time traffic (voice, video, interactive sessions) |
📶 Benefits of the Dedicated TURN IP Range
-
Optimized for Azure Virtual Desktop & Windows 365
Dedicated IP routing reduces contention and avoids unnecessary filtering or proxy interference. -
Enhanced Security Control
Organizations can explicitly whitelist TURN traffic without affecting other services using ACS. -
Better Routing Behavior
Allows direct, local breakout and integration with Microsoft’s low-latency global backbone. -
Easier Management
The inclusion in theWindowsVirtualDesktopservice tag simplifies network rule enforcement in both on-prem and cloud firewalls.
🌍 Supported TURN Relay Regions
Relays are now deployed in 40 strategic locations, covering every major Azure geography.
Selection is based on the user’s physical location, not the virtual host:
-
EMEA: UK South/West, France Central, Germany West Central, Norway East, Sweden Central, Switzerland North, UAE Central/North, Poland Central, Italy North
-
AMERICAS: East US, East US 2, West US, West US 2/3, Central US, South Central US, West Central US, North Central US, Canada Central/East, Brazil South, Mexico Central
-
ASIA & PACIFIC: Japan East/West, Korea Central/South, Taiwan North, Southeast Asia, Central India, South India, Australia East/Southeast
-
AFRICA: South Africa North/West
⚠️ When a region is unavailable, the connection may fall back to TCP, impacting session performance.
🛠 How to Prepare: Action Required
To avoid service interruptions, network administrators must explicitly allow and optimize traffic to the new TURN IP range (51.5.0.0/16).
✅ Step 1: Ensure Accessibility
-
Allow outbound access to
51.5.0.0/16on all egress devices. -
Confirm the IP range is reachable from all relevant endpoints, especially if using custom firewalls or security appliances.
-
For hosted network deployments (Windows 365), this is preconfigured.
-
For AVD/ANC deployments, the
WindowsVirtualDesktopservice tag covers this range.
✅ Step 2: Optimize Routing
To maintain low latency and reliability, traffic must be optimized:
| Requirement | Why |
|---|---|
| No TLS Inspection | TURN uses double encryption (TLS-in-TLS); inspection adds latency and can cause instability |
| Local Internet Breakout | Direct egress ensures shortest path to Microsoft’s backbone |
| Bypass VPN/Proxies/SWG | These introduce delay and may block TURN traffic; configure split tunneling or exclusions |
| Use UDR for Cloud-based VMs | Route TURN traffic directly to Internet, not through virtual appliances |
🔧 Sample Configuration Guidance
📚 Learn More
🔖 Summary
| What’s Changing | New dedicated TURN range 51.5.0.0/16 replacing ACS range 20.202.0.0/16 |
|---|---|
| Action Needed | Configure bypass rules and ensure routing optimizations for new subnet |
| Key Benefits | Lower latency, improved reliability, simplified security control, and expanded global coverage |
Let this be part of your June 2025 change management schedule. Neglecting to update routing or firewall policies may result in degraded user experience across AVD and Windows 365 sessions.