# that is not an real project (non real company non ral portal) and just a fun idea to do something best of the best according of Microsoft tech (at least why not?)
So let’s go!
In modern corporate systems (especially for companies with 10,000+ employees), secure and scalable authentication is critical. This article demonstrates how to implement Application Identity in Microsoft Entra ID (formerly Azure AD) for an HR portal automating personnel processes.
We cover:
-
Enterprise-scale solution architecture
-
Step-by-step configuration with code examples (C#, PowerShell)
-
Security and performance best practices
-
Real-world HR automation use cases
1. Business Context: What Does This Solution Achieve?
For “ExampleCorp” (10,000 employees), the system provides:
HR Process Automation
| Function | Technology | HR Time Savings |
|---|---|---|
| User account creation | Microsoft Graph sync | 200+ hrs/month |
| Account deactivation | Azure Automation + Entra ID | 100% compliance |
| Employee onboarding portal | React + Entra ID auth | 30% fewer IT tickets |
Technical Advantages
No user context required – Background processes run 24/7
Certificates instead of passwords – Enterprise-grade security
Scalability – Supports 100K+ users
2. Solution Architecture
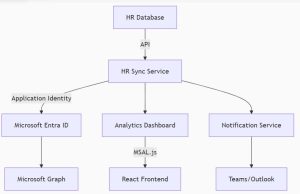
Key Components
-
HR Sync Service – .NET Core Background Service
-
Auth Layer – MSAL + Certificates
-
Monitoring – Azure Sentinel + Log Analytics
3. Step-by-Step Implementation
3.1. App Registration in Entra ID
PowerShell (for enterprise automation):
Connect-MgGraph -Scopes "Application.ReadWrite.All" # Create application $app = New-MgApplication -DisplayName "HR Portal PROD" ` -SignInAudience "AzureADMyOrg" ` -Web @{ RedirectUris = "https://hr.examplecorp.com/auth"; } # Configure certificates (not secrets!) $cert = New-SelfSignedCertificate -Subject "CN=HR Portal Auth" -KeySpec KeyExchange $params = @{ KeyCredentials = @( @{ Type = "AsymmetricX509Cert"; Usage = "Verify"; Key = [System.Convert]::ToBase64String($cert.GetRawCertData()) } ) } Update-MgApplication -ApplicationId $app.Id -BodyParameter $params
3.2. API Permissions
C#
var scopes = new[] { "User.ReadWrite.All", // User management "GroupMember.Read.All", // Org structure access "Mail.Send", // Notifications "Directory.Read.All" // Organizational data };
3.3. Sync Service Implementation (C#)
public class UserSyncService : BackgroundService { private readonly GraphServiceClient _graph; protected override async Task ExecuteAsync(CancellationToken ct) { var authProvider = new CertificateAuthProvider( tenantId: Configuration["Entra:TenantId"], clientId: Configuration["Entra:ClientId"], certificate: LoadCertificate()); _graph = new GraphServiceClient(authProvider); while (!ct.IsCancellationRequested) { await SyncNewHiresAsync(); // New employee sync await SyncTerminationsAsync(); // Termination handling await Task.Delay(TimeSpan.FromHours(1), ct); } } private async Task SyncNewHiresAsync() { var newUsers = await _hrApi.GetNewHiresAsync(); foreach (var user in newUsers) { await _graph.Users.Request().AddAsync(new User { DisplayName = user.FullName, UserPrincipalName = $"{user.Id}@examplecorp.com", AccountEnabled = true, PasswordProfile = new PasswordProfile { ForceChangePasswordNextSignIn = true, Password = GenerateTemporaryPassword() } }); } } }
4. Enterprise Security
4.1. Conditional Access Policies
{ "displayName": "HR Portal Access Policy", "conditions": { "applications": { "includeApplications": ["your-app-id"] }, "locations": { "includeLocations": ["Corporate-IP-Range"] } }, "grantControls": { "operator": "AND", "builtInControls": ["mfa", "compliantDevice"] } }
4.2. Monitoring with KQL (Azure Sentinel)
SigninLogs | where AppId == "your-app-id" | where ResultType != "0" | project TimeGenerated, UserPrincipalName, IPAddress, ResultDescription | join kind=inner (AuditLogs | where OperationName == "Add user") on $left.UserPrincipalName == $right.TargetResources.userPrincipalName
4.3. Certificate Rotation
# Automated rotation via Key Vault $newCert = New-AzKeyVaultCertificate -VaultName "hr-kv" -Name "hr-auth-cert" -Policy @{ SecretProperties = @{ ContentType = 'application/x-pkcs12' } KeyProperties = @{ Exportable = $true; KeyType = 'RSA' } }
5. Performance at 10K+ Scale
Optimizations:
-
Token caching: MSAL defaults to 60-minute cache
-
Batch processing: Handle users in groups of 500
for (int i = 0; i < users.Count; i++) { batch.AddBatchRequestStep(new BatchRequestStep( $"user{i}", _graph.Users.Request().GetHttpRequestMessage(), null )); } await _graph.Batch.Request().PostAsync(batch);
Conclusion
Implementing Application Identity authentication in Microsoft Entra ID provides:
-
Security: Certificates + Conditional Access
-
Scalability: 100K+ user support
-
Automation: End-to-end HR processes without manual intervention
Implementation roadmap:
-
Pilot in test tenant
-
Start with read-only permissions
-
Gradually expand functionality
ROAD MAP
Phase 0: Preparation (Weeks 1-2)
Objective: Define scope, stakeholders, and security requirements.
Tasks
-
Stakeholder Workshops
-
HR: Identify pain points (onboarding/offboarding delays, reporting needs)
-
IT: Review security policies and infrastructure constraints
-
-
Technical Discovery
-
Inventory existing HR systems (Workday/SAP/1C)
-
Document Microsoft Entra ID tenant configuration
-
-
Compliance Review
-
GDPR/local data protection laws
-
Internal audit requirements
-
Deliverables:
Project charter
High-level architecture diagram
Phase 1: Core Implementation (Weeks 3-8)
Objective: Build and test the authentication backbone.
Milestone 1.1: Entra ID App Configuration
-
Register application with certificate-based auth (PowerShell automation)
-
Configure API permissions (
User.ReadWrite.All,Mail.Send) -
Set up Conditional Access policies (IP restrictions, MFA for admins)
Milestone 1.2: Sync Service Development
-
Implement background service (.NET Core) for:
-
User provisioning/de-provisioning
-
Org structure sync (Teams/SharePoint groups)
-
-
Integrate with HR system API
Milestone 1.3: Monitoring Baseline
-
Azure Sentinel alerts for anomalous sign-ins
-
Log Analytics dashboards for sync job status
Deliverables:
Working sync service (test environment)
Security audit report
Phase 2: Pilot Deployment (Weeks 9-12)
Objective: Validate with a controlled user group.
Tasks
-
Deploy to UAT environment with 50 test users
-
Test scenarios:
-
New hire auto-provisioning
-
Termination access revocation
-
Manager approval workflows
-
-
Conduct penetration testing
Success Metrics:
✔ 100% automated account creation
✔ Zero manual IT tickets for test group onboarding
Phase 3: Enterprise Rollout (Weeks 13-20)
Objective: Full deployment with scalability enhancements.
Stage 3.1: Gradual Deployment
-
Roll out by department (prioritize high-turnover teams first)
-
Batch processing for initial 10K user sync
Stage 3.2: Performance Tuning
-
Load test with 10K concurrent users
-
Optimize token caching and Graph API batch requests
Stage 3.3: Training & Documentation
-
Admin training: Certificate rotation, incident response
-
User guides: Self-service password reset
Deliverables:
Production deployment sign-off
Runbooks for IT operations
Phase 4: Optimization & Scale (Ongoing)
Objective: Continuous improvement.
Quarterly Activities
-
Certificate rotation automation (Key Vault integration)
-
Review audit logs for unused permissions
-
Expand integrations (e.g., payroll system sync)
Risks & Mitigation
| Risk | Mitigation Strategy |
|---|---|
| HR data inconsistencies | Implement reconciliation jobs |
| Certificate expiration | Azure Monitor alerts 30 days prior |
| Graph API throttling | Exponential backoff retry logic |
Timeline Summary
![]()
or like that
gantt
title Project Timeline
dateFormat YYYY-MM-DD
section Core
Preparation :done, p1, 2024-01-01, 14d
Implementation :active, p2, after p1, 42d
section Deployment
Pilot :p3, after p2, 28d
Enterprise Rollout: p4, after p3, 56d
RACI Matrix
(Responsible, Accountable, Consulted, Informed)
| Task | IT Team | HR Team | Security | External Vendor | Project Manager |
|---|---|---|---|---|---|
| Entra ID App Registration | R | C | A | – | I |
| Certificate Management | R | – | A | C (CA Vendor) | I |
| Sync Service Development | R | C | C | – | A |
| Conditional Access Policies | A | – | R | – | I |
| Pilot User Testing | S | R | I | – | A |
| Penetration Testing | C | – | R | R (3rd Party) | A |
| Production Deployment | R | A | C | – | A |
| User Training | C | R | – | – | I |
Key:
-
R = Responsible (executes the work)
-
A = Accountable (final approval)
-
C = Consulted (provides input)
-
I = Informed (receives updates)
Budget Breakdown
*(For 10,000+ Employee Implementation)*
| Category | Cost Estimate | Details |
|---|---|---|
| Development | $120,000 | .NET Core sync service, React dashboard, and API integrations |
| Microsoft Licensing | $25,000/year | Entra ID P2, Azure Premium (for Conditional Access/MFA) |
| Security | $40,000 | Penetration testing, Sentinel monitoring setup, compliance audits |
| Infrastructure | $18,000/year | Azure VMs, Key Vault, Log Analytics |
| Training | $15,000 | Admin workshops + user self-service guides |
| Contingency (15%) | $32,700 | Unplanned scope changes or additional security requirements |
| Total | $250,700 |
Cost-Saving Opportunities:
-
Use existing Azure credits (if available)
-
Phase rollout to defer licensing costs
-
Internal training instead of vendor-led
to be continue
