By 2026 artificial intelligence is no longer something that security teams discuss in strategy decks or conference talks. It is something they encounter on a Monday morning when alerts start coming in before anyone has finished their coffee. AI quietly changed the rhythm of attacks. There is no preparation phase anymore. No clear start. No obvious spike. Attacks simply exist in the background like network noise and occasionally they succeed.
What changed is not only sophistication but persistence. An attacker does not need a lucky guess or a brilliant exploit. They need time and AI provides unlimited time. A model can test authentication flows continuously rotate IPs vary behaviour and slowly map where the organisation forgot to clean up something old. That forgotten service account created three years ago for a temporary integration is no longer temporary. It becomes the front door.
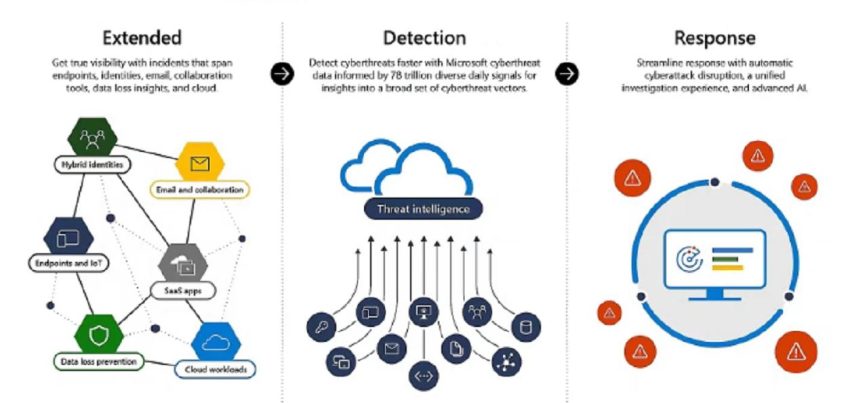
Microsoft in 2026 seems to design its security stack with this exact scenario in mind. There is very little romance left in the narrative. No talk about stopping every attack. The tone is closer to engineering than heroism. Systems will be touched. Credentials will leak. What matters is how fast this becomes visible and how little damage it causes.
This is where Microsoft Security Copilot starts to feel less like a product and more like a necessary layer. In real SOC work one of the most expensive things is not malware. It is time spent understanding what is actually happening. Analysts jump between Defender alerts identity logs mailbox activity cloud audit trails and conditional access decisions. Each tool is correct in isolation and confusing in combination. Security Copilot in 2026 sits across these signals and translates machine telemetry into something closer to human reasoning.
A very typical example looks like this. A user logs in successfully from a location they have used before. Nothing is blocked. Ten minutes later there is a token refresh from a cloud workload. Then a mailbox rule is created. None of these events are fatal alone. Together they form a pattern that experienced analysts recognise immediately. The problem is that by the time a human notices it the attacker may already be moving laterally. Copilot does not invent intelligence here. It compresses time. It shows the pattern while it is still forming.
The defensive muscle underneath this reasoning is still Microsoft Defender. By 2026 Defender behaves very differently from classic endpoint security. It no longer treats identity endpoint and cloud as separate domains. A suspicious login is not just an Entra event. It becomes part of a behavioural model that also includes device posture process execution mailbox actions and API calls. When an attacker signs in successfully Defender does not panic. It watches. It waits for behaviour that deviates from the usual rhythm of that identity.
This matters because AI driven attacks are rarely noisy. They try to look boring. A PowerShell process launched by an administrator account is not alarming. A PowerShell process launched at three in the morning followed by token reuse and a privilege change request is a different story. Defender in 2026 is tuned to notice these stories rather than individual events.
Understanding the full story still requires context and that is where Microsoft Sentinel quietly changes its role. In earlier years SIEM platforms trained people to think in alerts and rules. By 2026 this model collapses under its own weight. There are too many signals and too much automation on the attacker side. Sentinel increasingly behaves like a reconstruction engine. It looks backward and forward. It answers questions that analysts actually ask. How did the attacker enter. What did they touch. Where do they still have access.
A very real example from enterprise environments is cloud lateral movement. An attacker compromises a user account with limited permissions. They discover a poorly scoped API permission in an application registration. That application has access to SharePoint sites the user never touched directly. Sentinel helps surface this indirect path. Not because it is a rule but because the sequence makes sense when viewed as a chain.
Identity is where most organisations still feel uncomfortable and Microsoft does not try to make this comfortable in 2026. With Microsoft Entra the philosophy is openly hostile. Every sign in is evaluated continuously. A successful authentication does not mean trust is established. It means trust is provisional. Session risk can change mid flight. Token lifetimes shrink. Conditional access reacts not just to who you are but to what you are doing right now.
This often surprises users. Someone opens a laptop at home signs in successfully and then suddenly loses access when the device posture changes or when behaviour drifts. From a usability standpoint this feels harsh. From a security standpoint it reflects reality. AI driven credential abuse does not respect office hours or good intentions.
Data is where many AI conversations become abstract until something breaks. In 2026 AI tools are embedded everywhere. People paste internal documents into assistants. Models summarise contracts generate reports and answer questions using corporate data. This is where Microsoft Purview stops being about compliance language and starts being about control. Purview defines which data can be used by AI systems and under which conditions. It reduces the risk that sensitive information quietly leaks through legitimate looking prompts and responses.
A common real life scenario is a well meaning employee asking an AI assistant to summarise customer complaints or financial results. Without governance the model may pull more data than intended. With Purview the scope is constrained. The AI still works but it works inside boundaries that humans often forget to apply manually.
Endpoints remain stubbornly relevant despite all the talk about cloud and AI. Laptops are lost. Devices are shared. Systems fall out of compliance. In 2026 Microsoft Intune becomes part of access decisions rather than a background management tool. A healthy identity on an unhealthy device is no longer sufficient. Access is conditional on both.
This shows up in simple everyday moments. Someone tries to access internal resources from a personal device that has not been patched. Nothing dramatic happens. Access is simply not granted. There is no alert storm. Just a quiet refusal. It feels mundane and that is exactly the point.
What becomes clear when looking at Microsoft in 2026 is not a single technological breakthrough but a shift in expectations. The company designs its security ecosystem for a world where pressure never stops. AI does not create smarter attackers as much as it creates tireless ones. Microsoft responds by trying to remove fatigue from defence. Not by replacing humans but by making their time matter again.
There is no promise of perfect safety here. No claim that AI will save everything. The message is subtler and more realistic. In 2026 security is about maintaining control while being constantly tested. Microsoft seems to accept that reality and builds accordingly.
RGDS,
Alex